Project: Streamlining Spring Boot Deployment on Demo Environment with IaaC and Configuration Management Tool on AWS Cloud.
Table of contents
Goal:
The goal of the project is to deploy a Spring Boot application on a demo environment with a minimal manual effort by utilizing Infrastructure as Code (IaaC) and configuration management tools. The project aims to automate the provisioning and configuration of the demo environment, including the creation of necessary infrastructure resources, installation of dependencies, and deployment of the Spring Boot application. The result is a simplified and efficient deployment process that reduces the potential for human error and increases the speed and consistency of application deployment on the demo environment.
Achievement:
Terraform to deploy the following AWS cloud services:
VPC
Public Subnets
Private Subnets
Launch Template
Auto Scaling Group of EC2 Machine with the Latest ubuntu image
Application Load Balancer for the above auto-scaling group
MySQL RDS
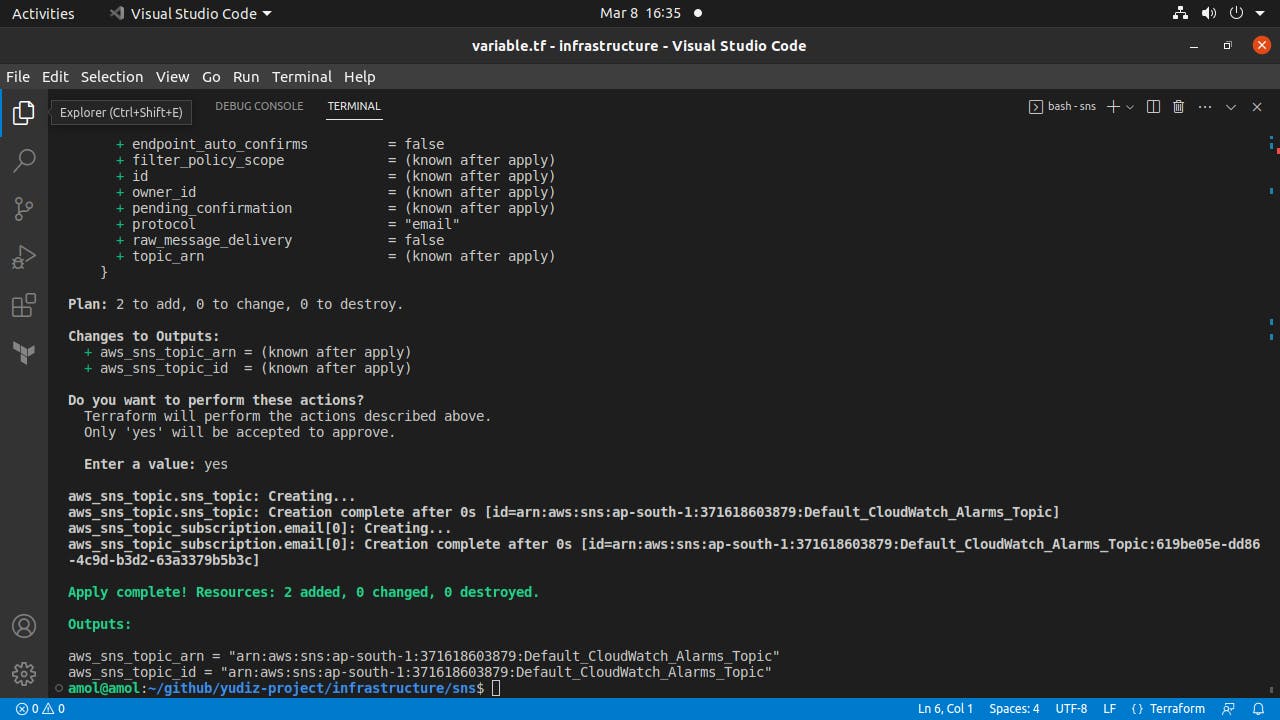
SNS Topic and subscription
Cloudwatch CPU and RAM utilization metric and Alert (Alerts should be sent to SNS Topic subscribers)
Deploying a sample application with the help of Ansible.
MySQL database connection with the application.
Application deployment on the auto-scaling group created using Terraform.
Following best practices while creating infrastructure.
Deployment with Validation:
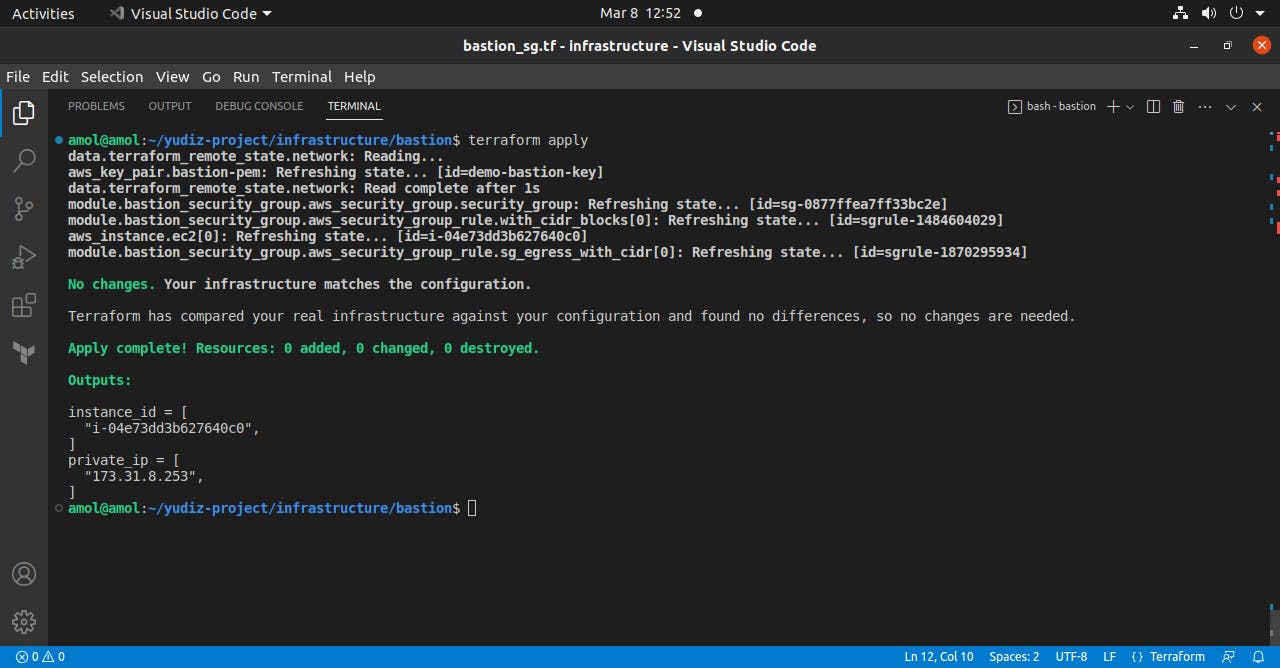
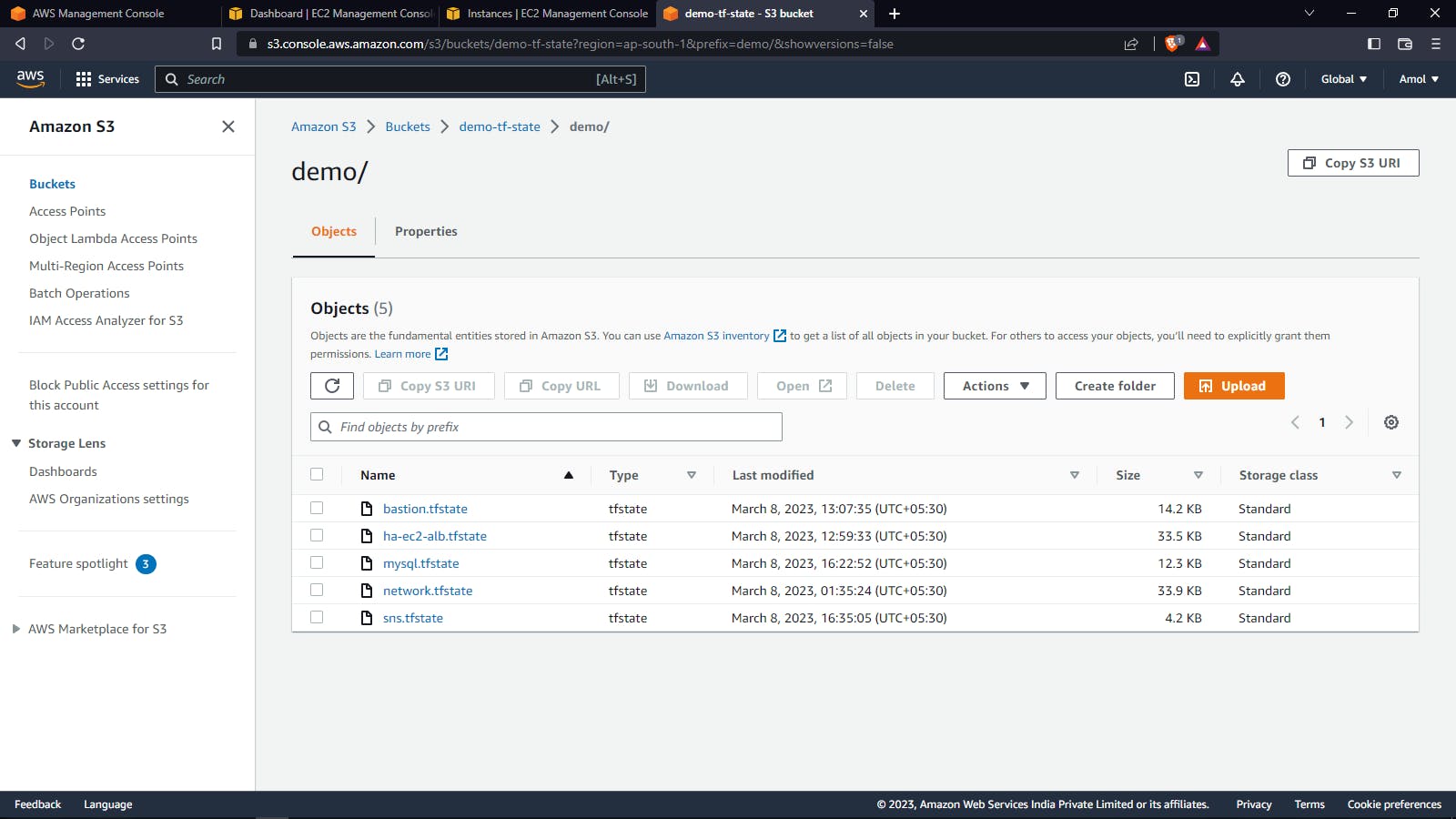
Configuring S3 as a backend to store state files remotely.
When multiple developers are working on the same infrastructure project, storing the state file remotely ensures that everyone is working with the latest version of the infrastructure code.
Storing the state file remotely ensures that the state file is not lost if the local machine crashes, and it makes it easier to recover the state file in case of accidental deletion.
Storing the state file remotely protects it from unauthorized access or tampering.
When multiple instances of Terraform are run concurrently, storing the state remotely ensures that they are not competing for access to the state file.
Storing the state file remotely allows for easy access from anywhere with an internet connection, which can be useful for remote work or working from multiple locations.
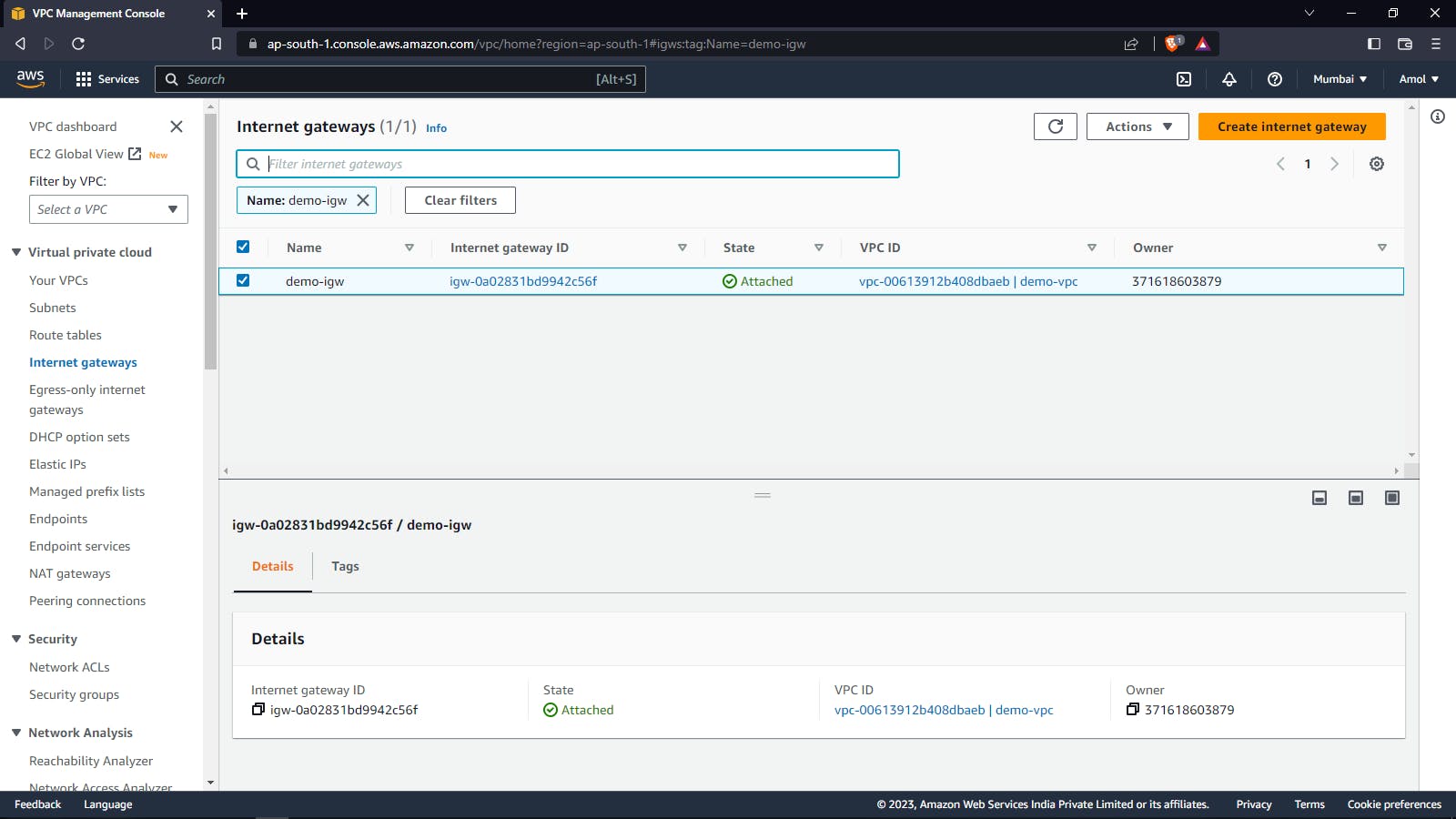
Creating a Network on AWS cloud with the help of Terraform code.
VPC: VPC stands for Virtual Private Cloud. It is a virtual network within the AWS cloud that allows users to launch AWS resources, such as EC2 instances, in a logically isolated and secure environment. VPCs can be customized with their IP address ranges, subnets, routing tables, and network gateways. They also provide a range of security features, such as network access control lists (ACLs) and security groups, to help users control access to their resources. In short, a VPC allows users to create a private virtual network in the AWS cloud.
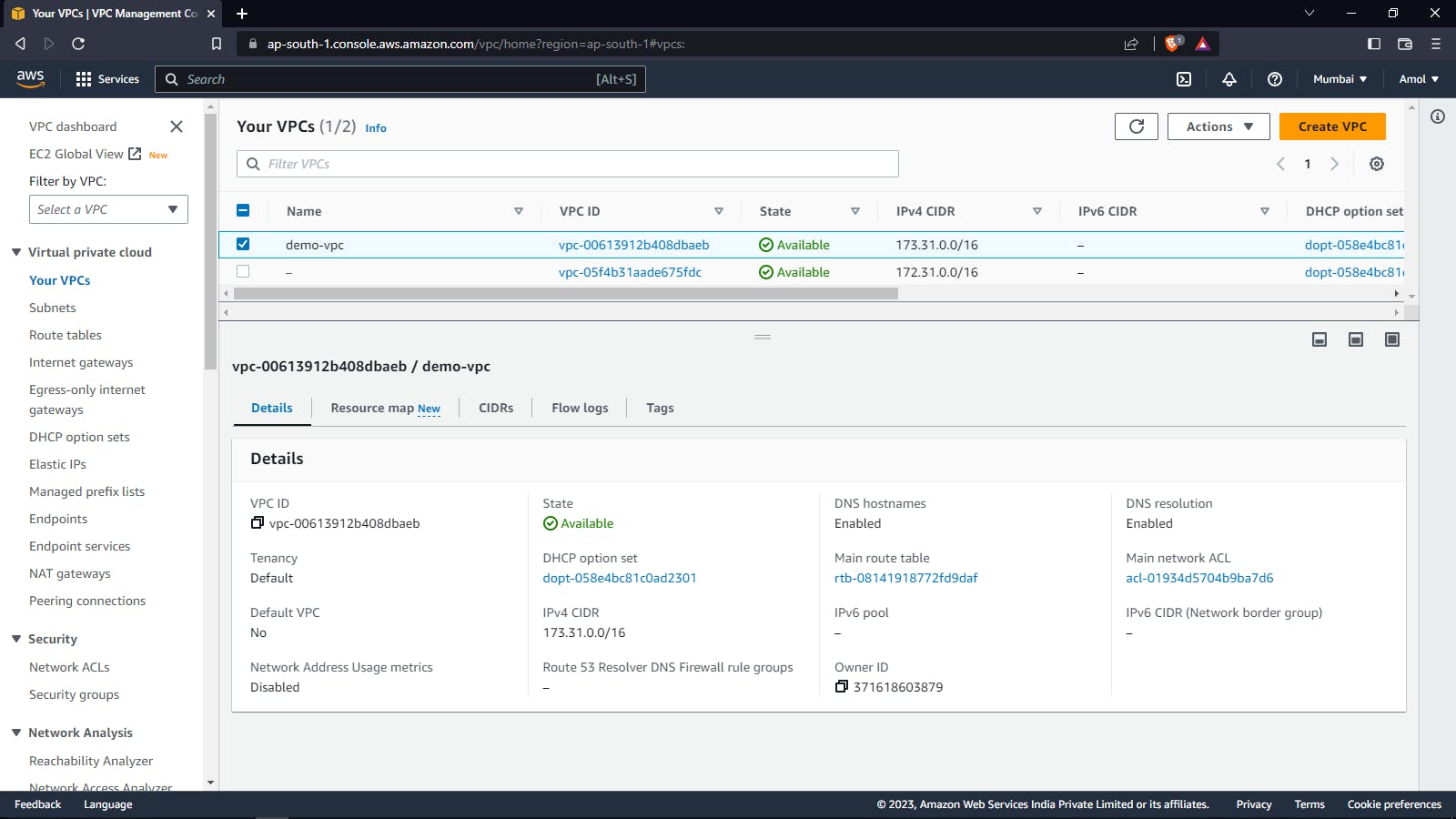
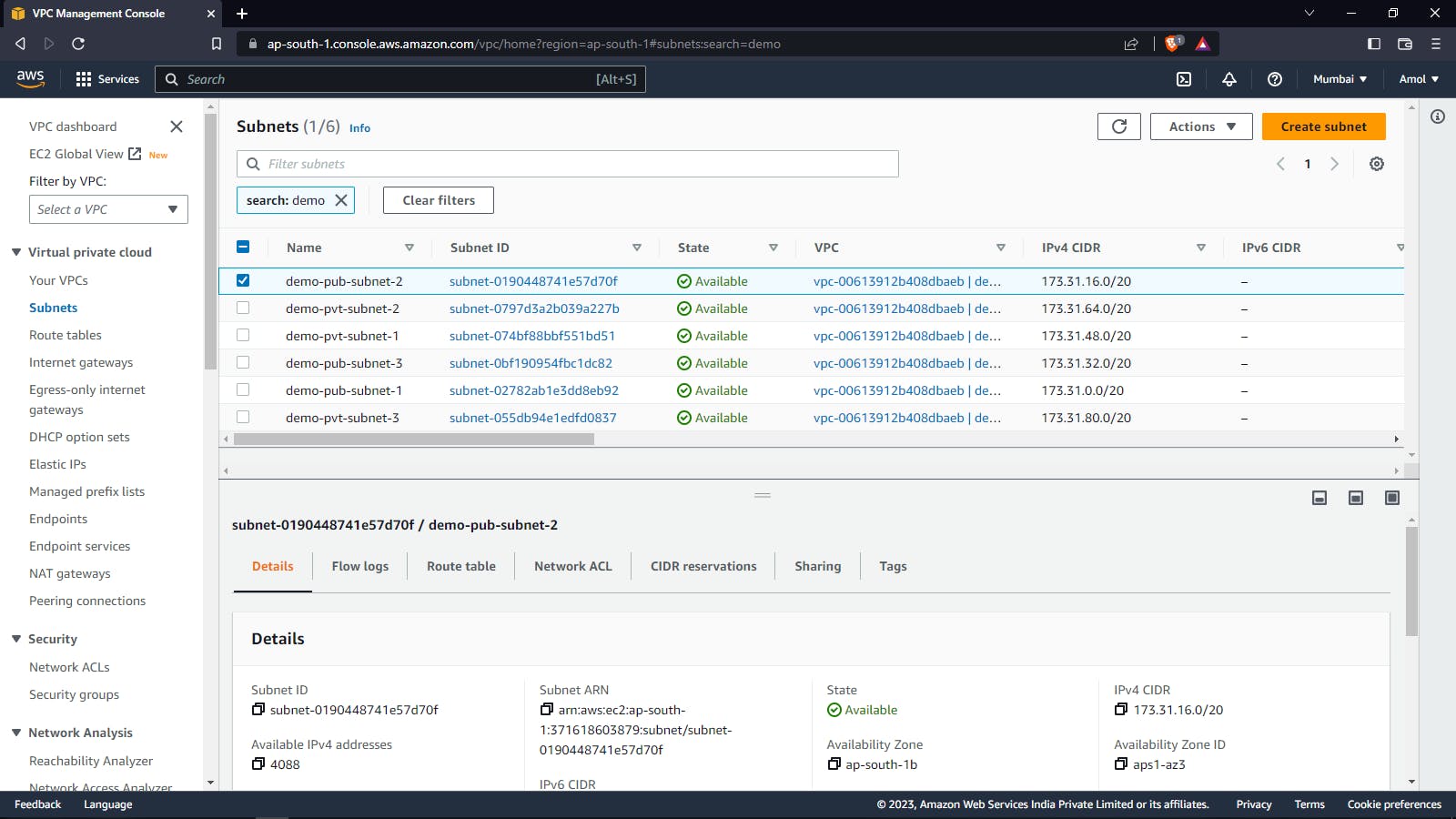
Public Subnets: Public subnets are subnets within an AWS Virtual Private Cloud (VPC) that have a route to the Internet Gateway (IGW) and can receive traffic from the public Internet. Resources deployed in a public subnet, such as EC2 instances, can have a public IP address and can communicate with the Internet directly, without any additional configuration.
Private Subnets: Private subnets are subnets within an AWS Virtual Private Cloud (VPC) that do not have a route to the Internet Gateway (IGW) and cannot receive traffic from the public Internet. Resources deployed in a private subnet do not have a public IP address and cannot communicate with the Internet directly, unless a specific configuration is in place, such as using a NAT Gateway. In our case scenario, we are using NAT Gateway.
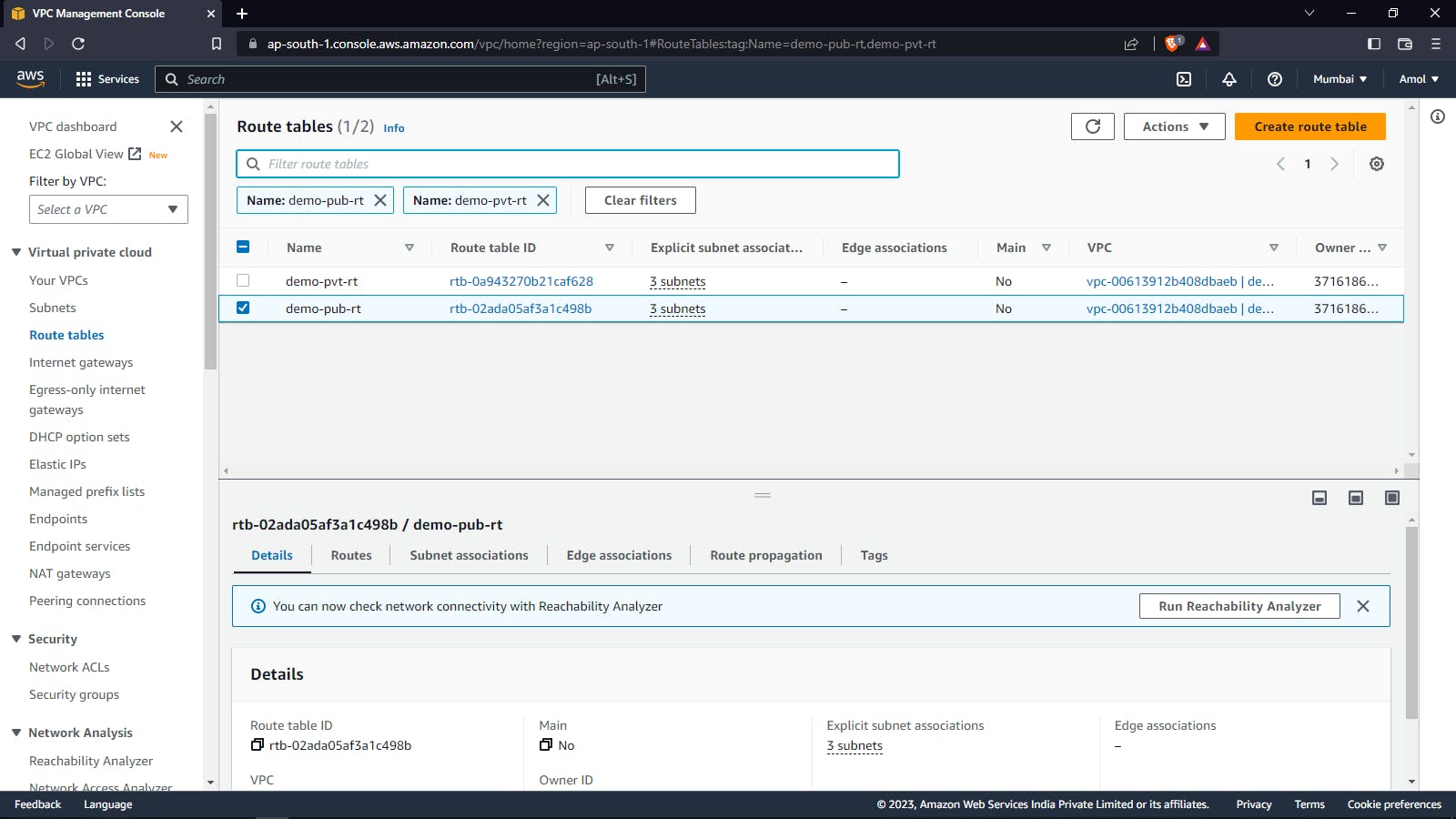
Public Route Table: A Public Route Table is a routing table within an AWS Virtual Private Cloud (VPC) that contains routes for directing traffic to and from the Internet Gateway (IGW). When a subnet within a VPC is associated with a Public Route Table, it allows the resources deployed in that subnet to have a public IP address and be accessible from the public Internet.
Private Route Table: A Private Route Table is a routing table within an AWS Virtual Private Cloud (VPC) that contains routes for directing traffic to and from private subnets that do not have a route to the Internet Gateway (IGW). When a subnet within a VPC is associated with a Private Route Table, it allows resources deployed in that subnet to communicate with other resources within the VPC and with resources in other VPCs that are connected through a NAT Gateway.
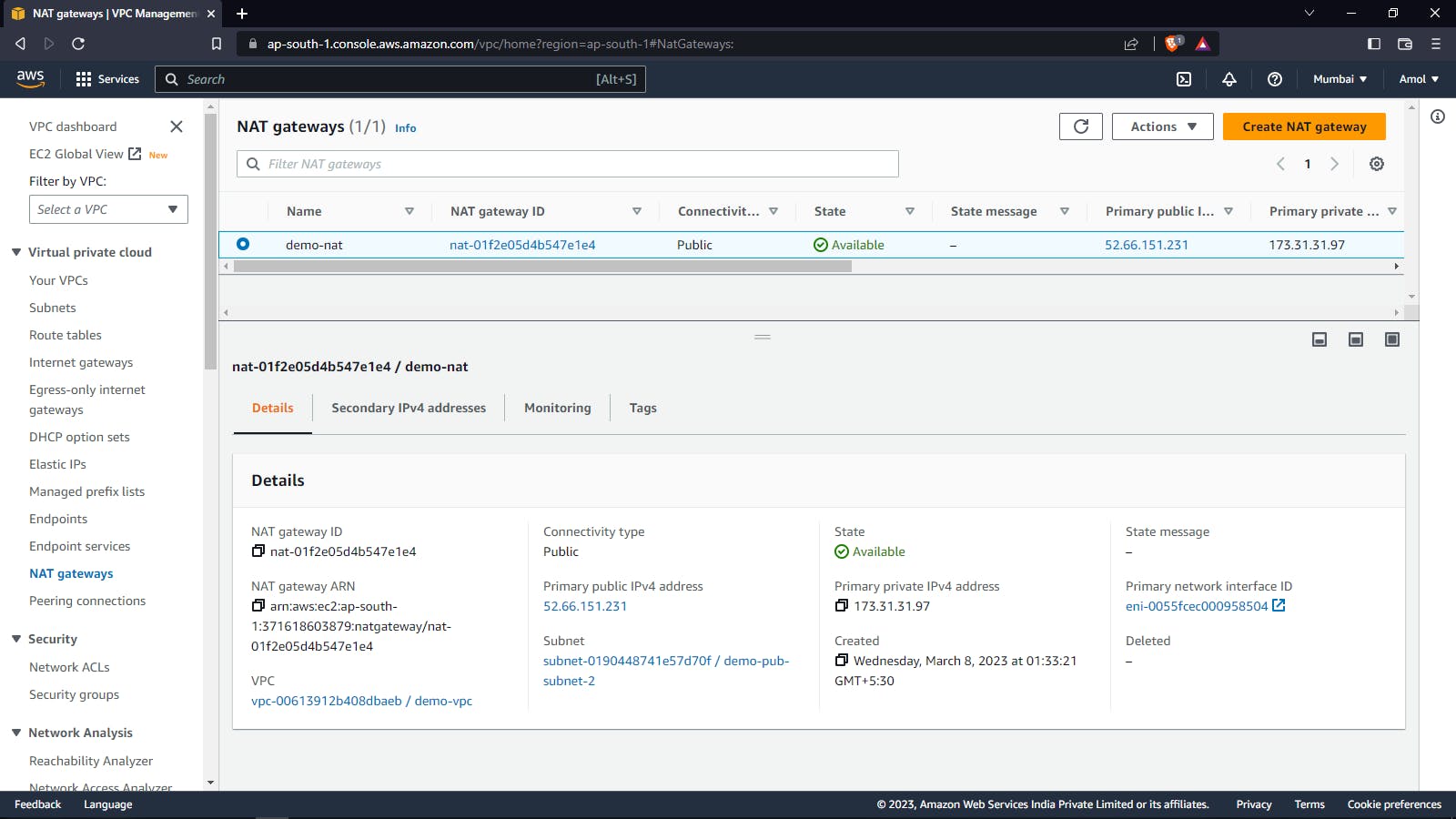
Public Application Loadbalancer: A Public Application Load Balancer (ALB) is an AWS service that allows you to distribute incoming traffic across multiple EC2 instances or other services within a VPC. It is called "public" because it has a public IP address and can be accessed from the Internet.
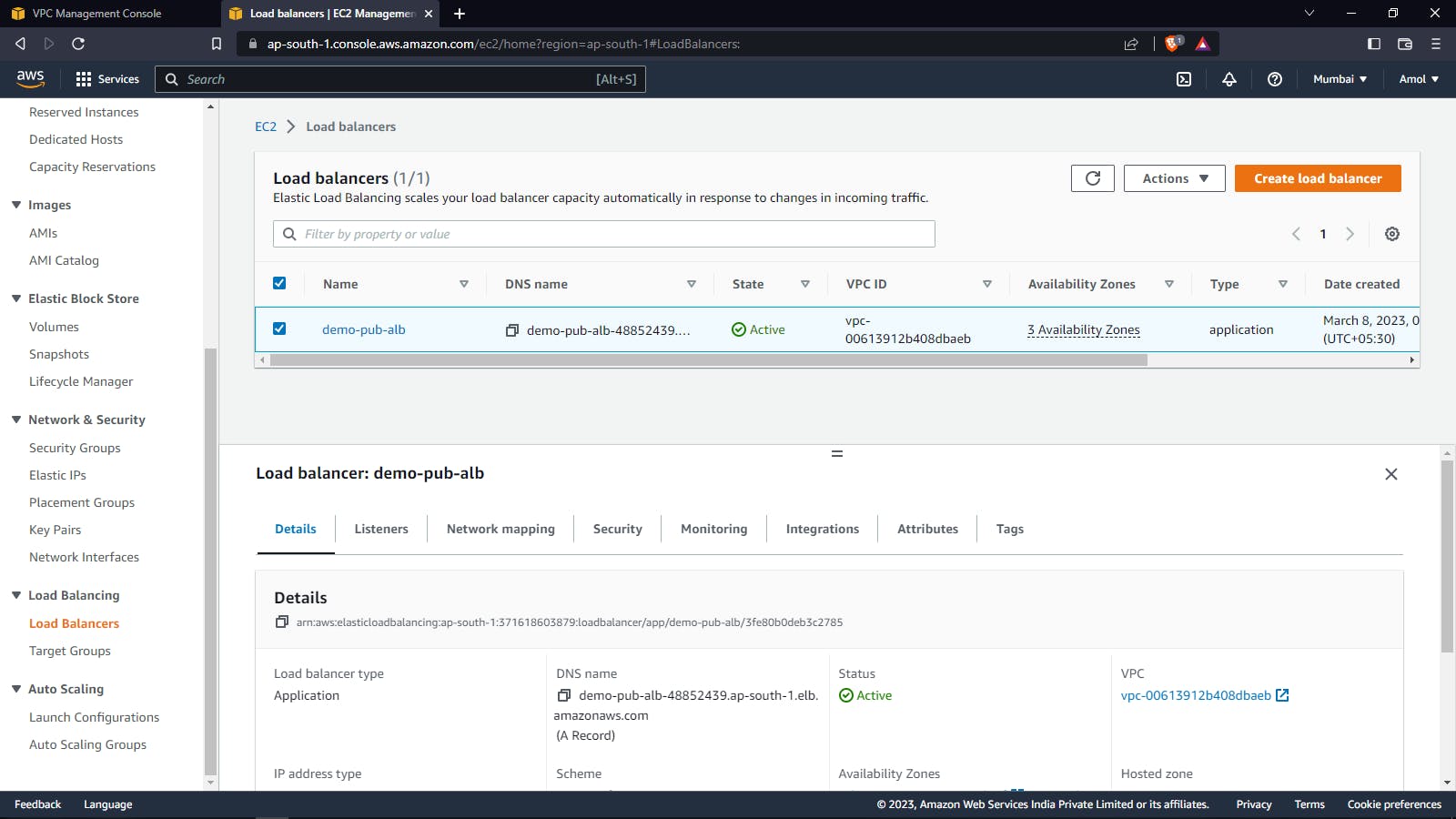
Security Group: A Security Group is a virtual firewall that controls inbound and outbound traffic for AWS resources, such as EC2 instances, within an AWS Virtual Private Cloud (VPC). It acts as a virtual barrier that determines what traffic is allowed to enter or leave an AWS resource based on a set of user-defined rules.
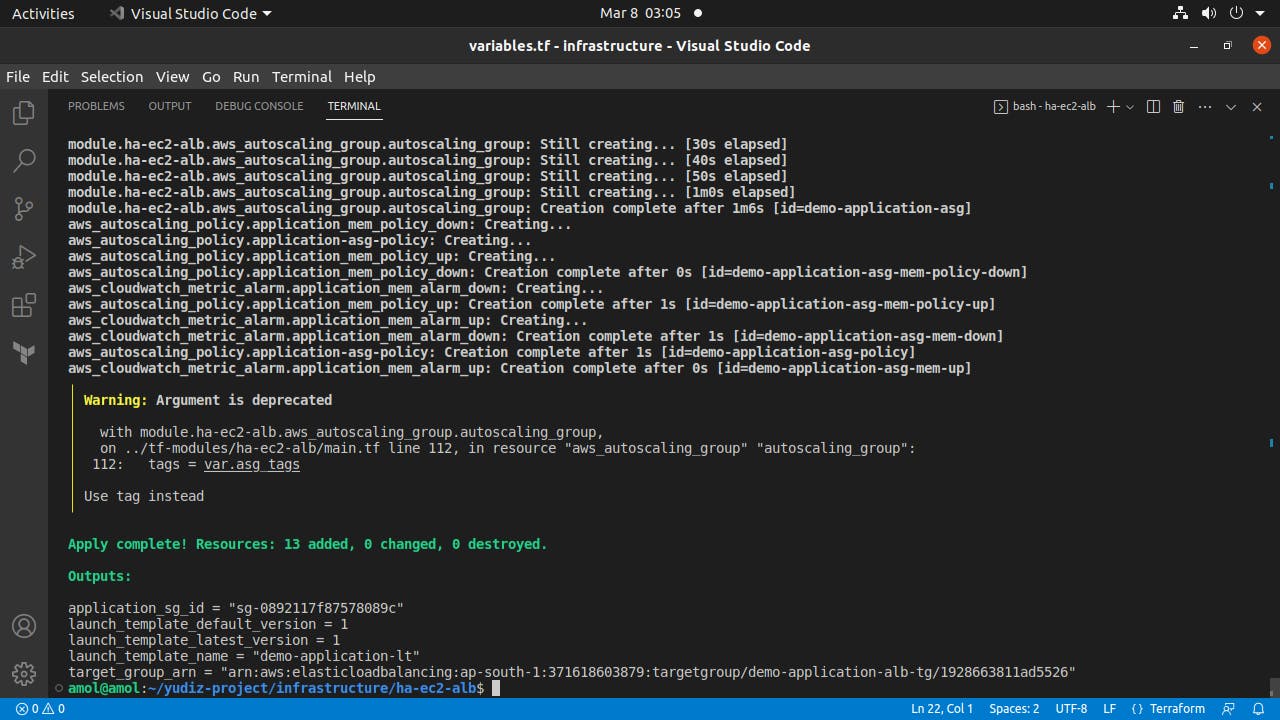
IaaC Automation: With the help of Terraform, we created the whole Network infrastructure in one go and also printed appropriate info as an output.
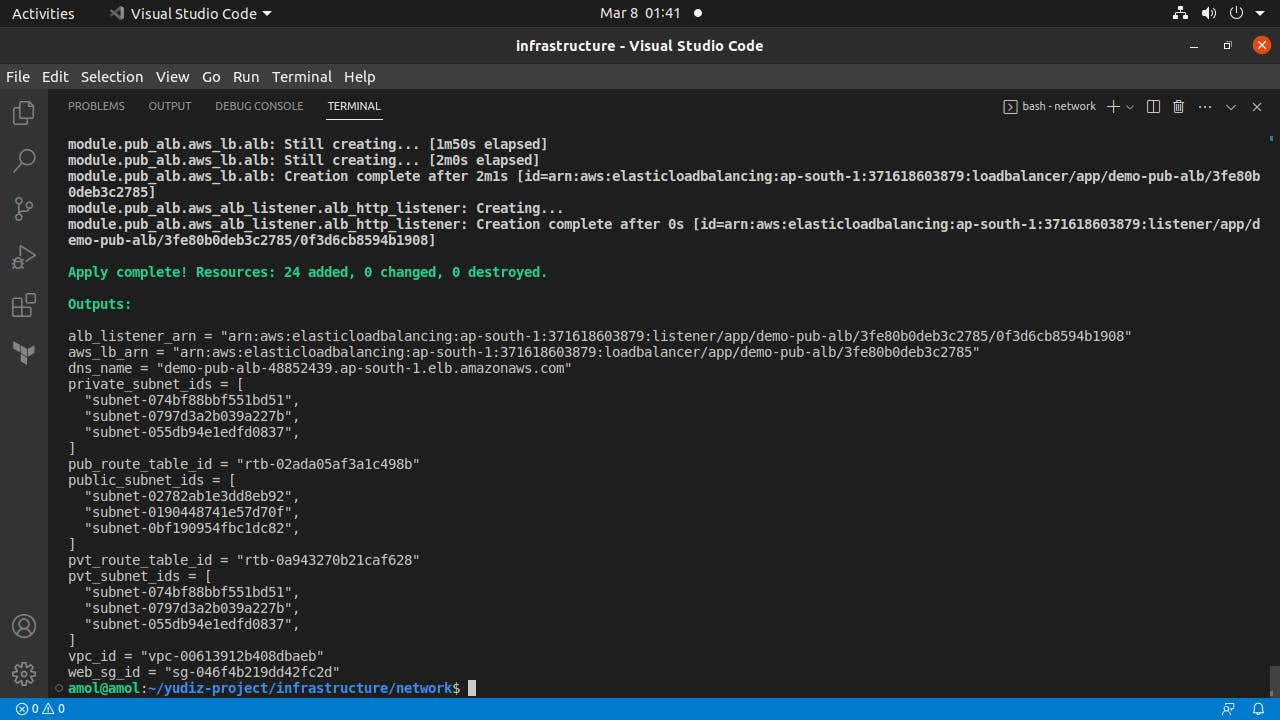
Creating HA-EC2_ALB Infrastrucure:
Creating High Availability EC2 Application Loadbalancer setup in Private Subnet.
Auto Scaling Group: An Auto Scaling group is an AWS service that allows you to automatically adjust the number of EC2 instances in a group based on changes in demand or traffic. It is designed to help you maintain optimal application performance and availability while minimizing costs by automatically scaling up or down in response to changes in traffic or demand.
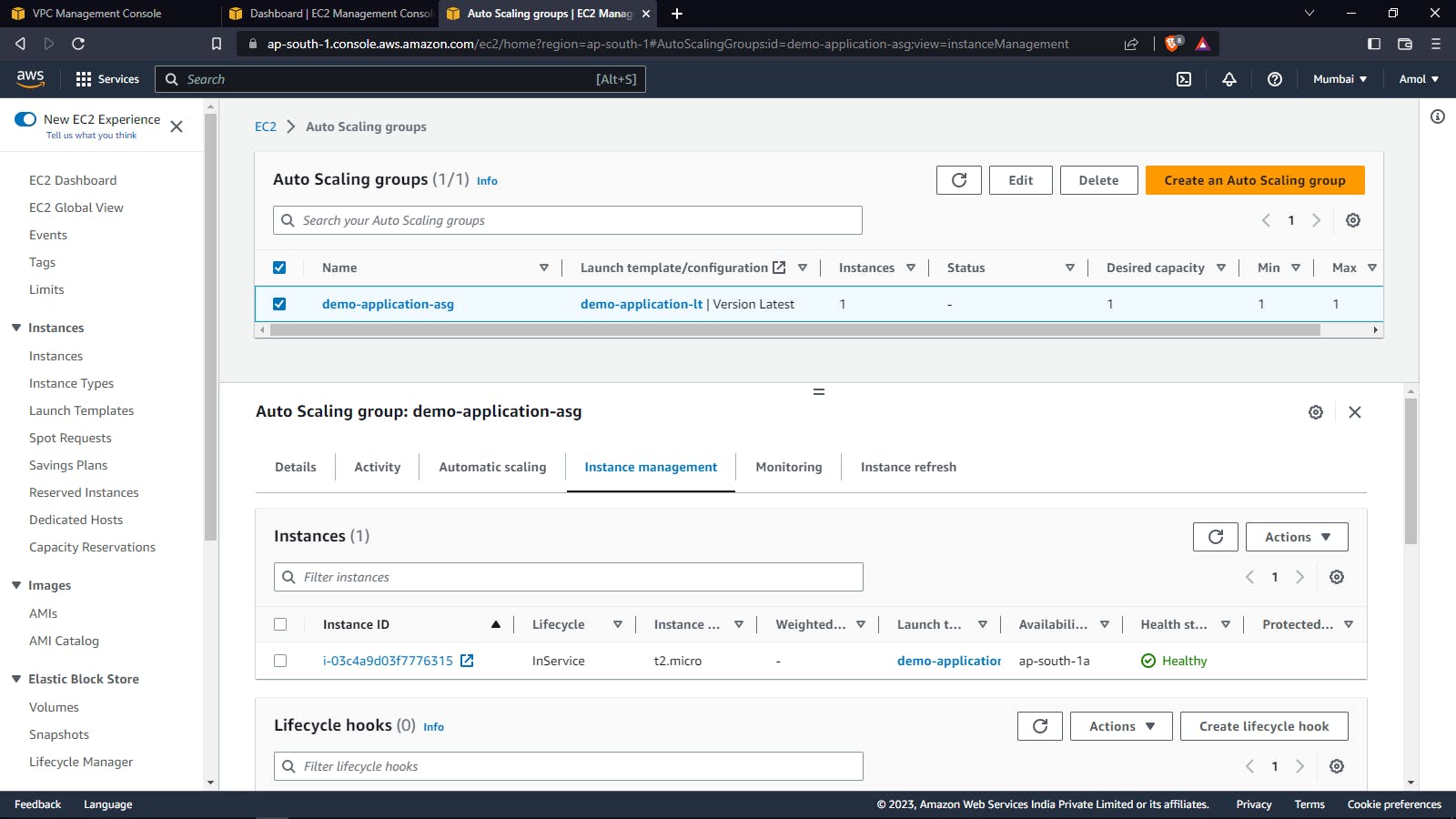
Target Group: When a load balancer receives incoming traffic, it routes the traffic to one or more target groups based on the rules you have configured. The target groups then forward the traffic to the instances or resources registered with them.
Target groups allow you to distribute traffic across multiple instances or resources, which can improve application performance, availability, and scalability. They also provide other features such as health checks, monitoring, and session stickiness.
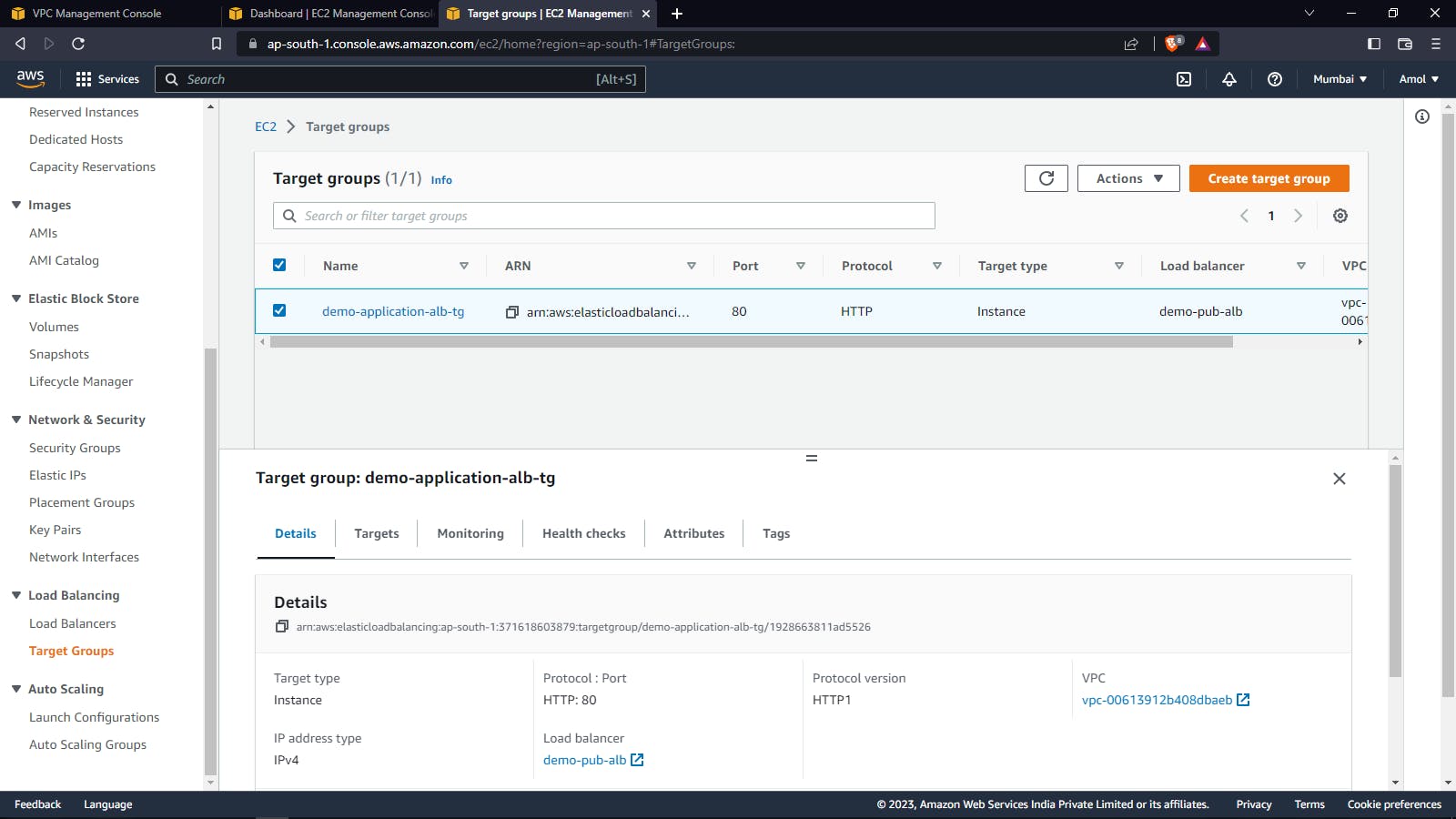
Creating Load Balancer listner rules
Automation with the help of the IaaC tool Terraform:
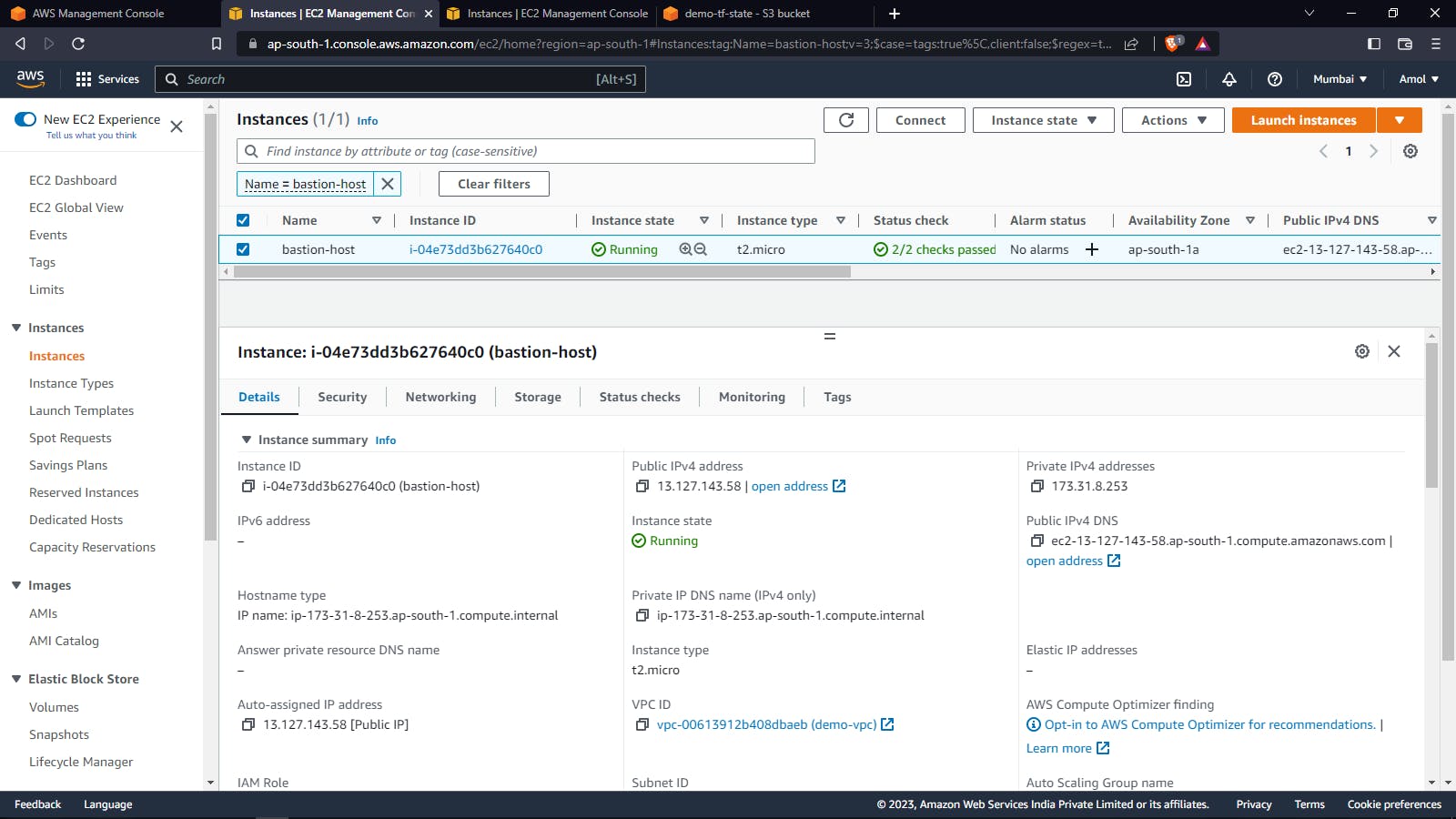
Bastion Host: The Bastion Host is often used as a jump server that allows secure access to other instances or resources in the private network without exposing them directly to the internet. This provides an additional layer of security by limiting the attack surface of the private network.
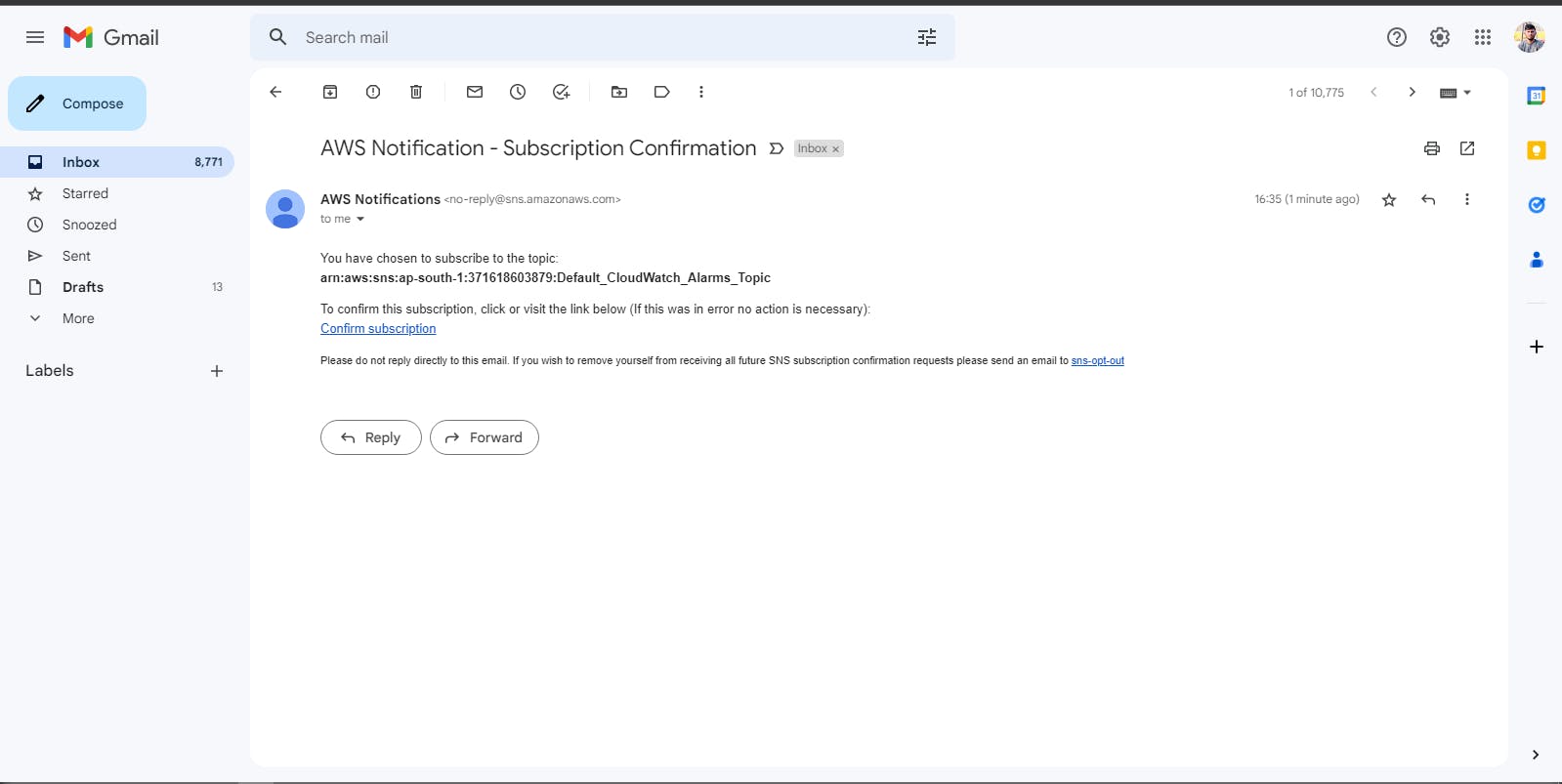
SNS Topic And Subscription Creation:
SNS Topic: SNS Topic is a communication channel that is used to deliver messages to subscribed endpoints or clients. Subscribers can be AWS Lambda functions, Amazon SQS queues, HTTP endpoints, mobile devices, email addresses, and other SNS topics.
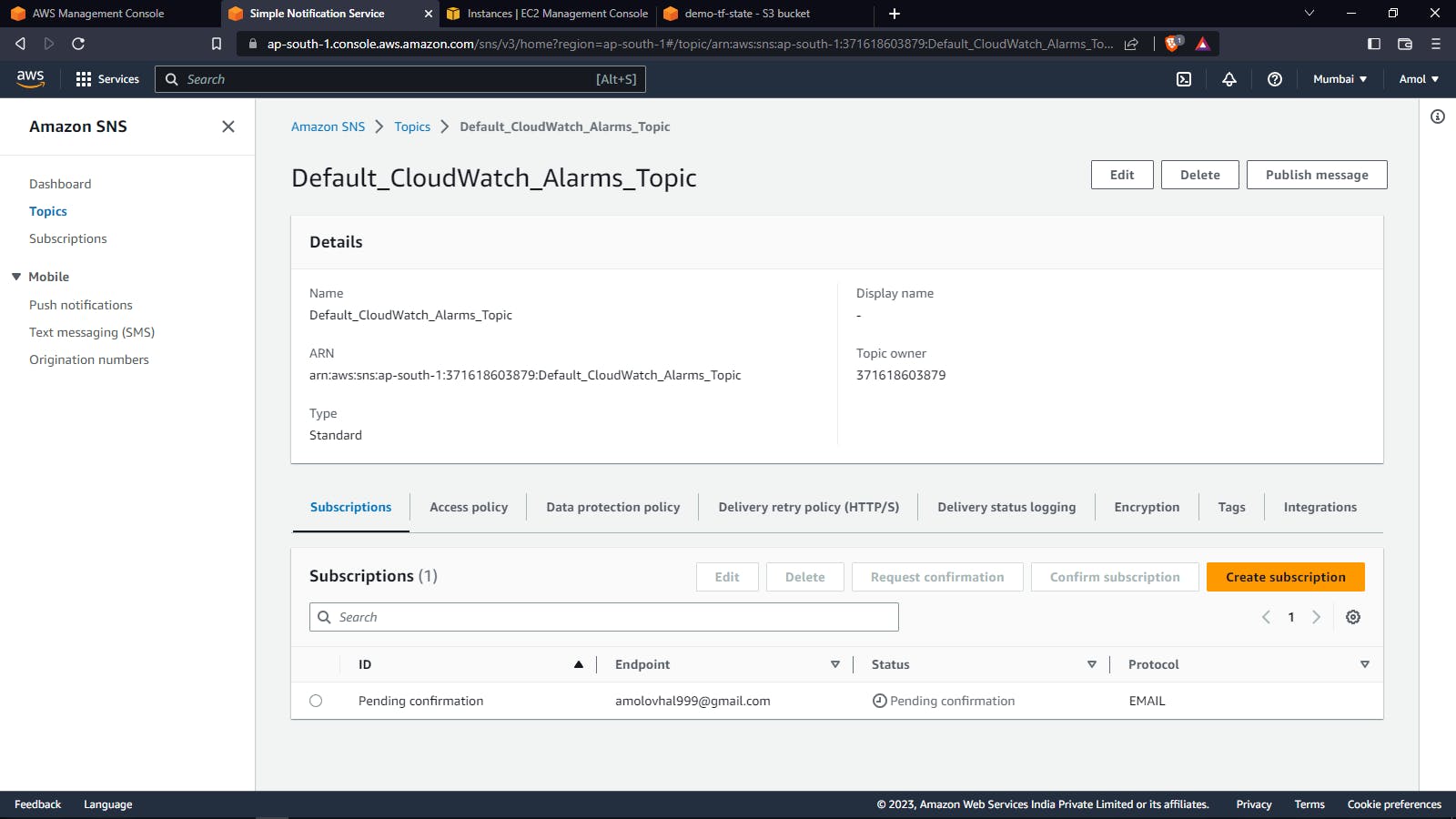
SNS Subscription: SNS subscription is a way to receive messages from an Amazon SNS topic. Subscribers can receive messages from a topic through various protocols, such as email, SMS, HTTP, HTTPS, Lambda, SQS, mobile push notifications, and other SNS topics.
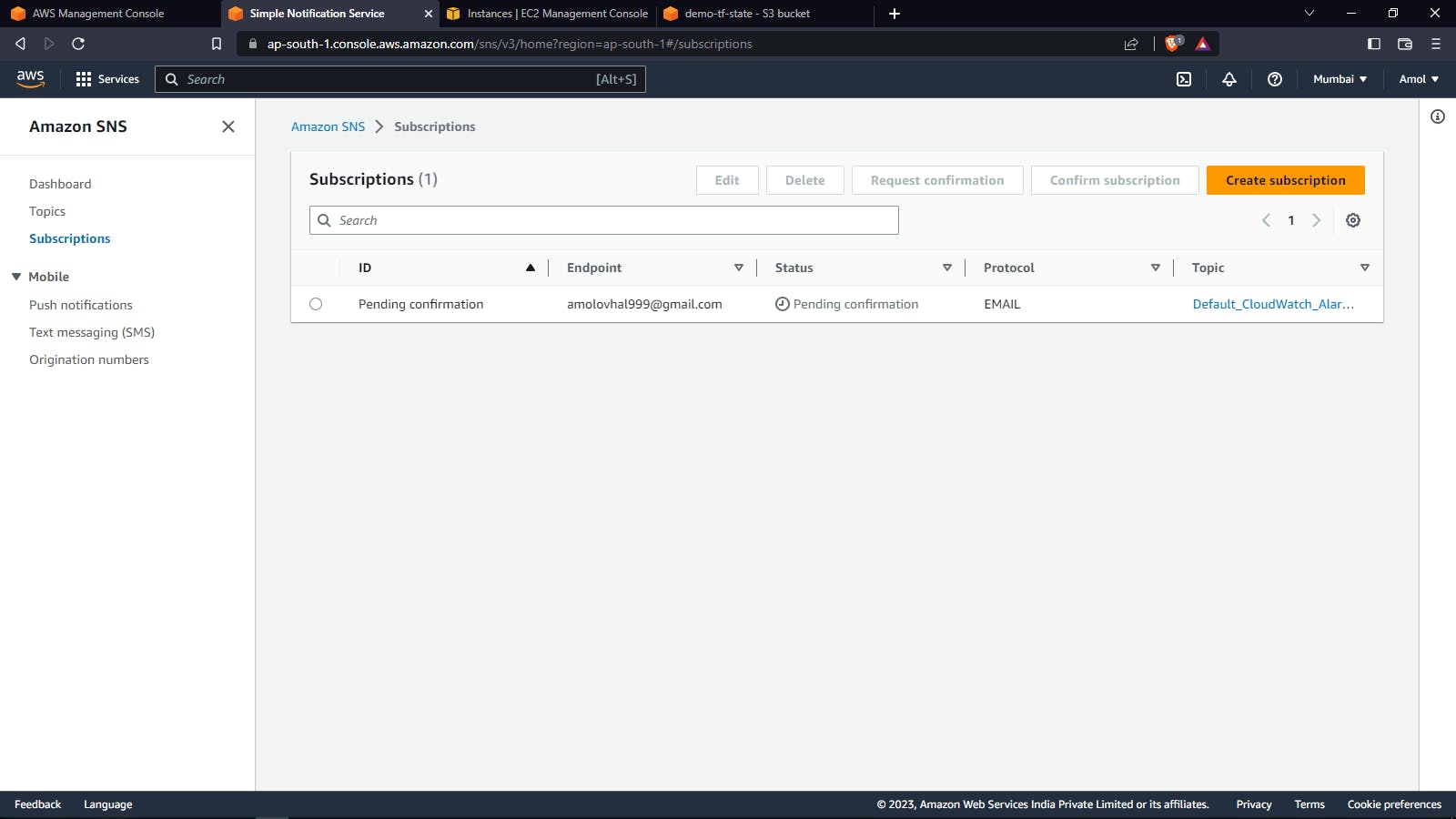
Validation: Here I got a mail from aws sns service.
Automation with the help of the IaaC tool Terraform:
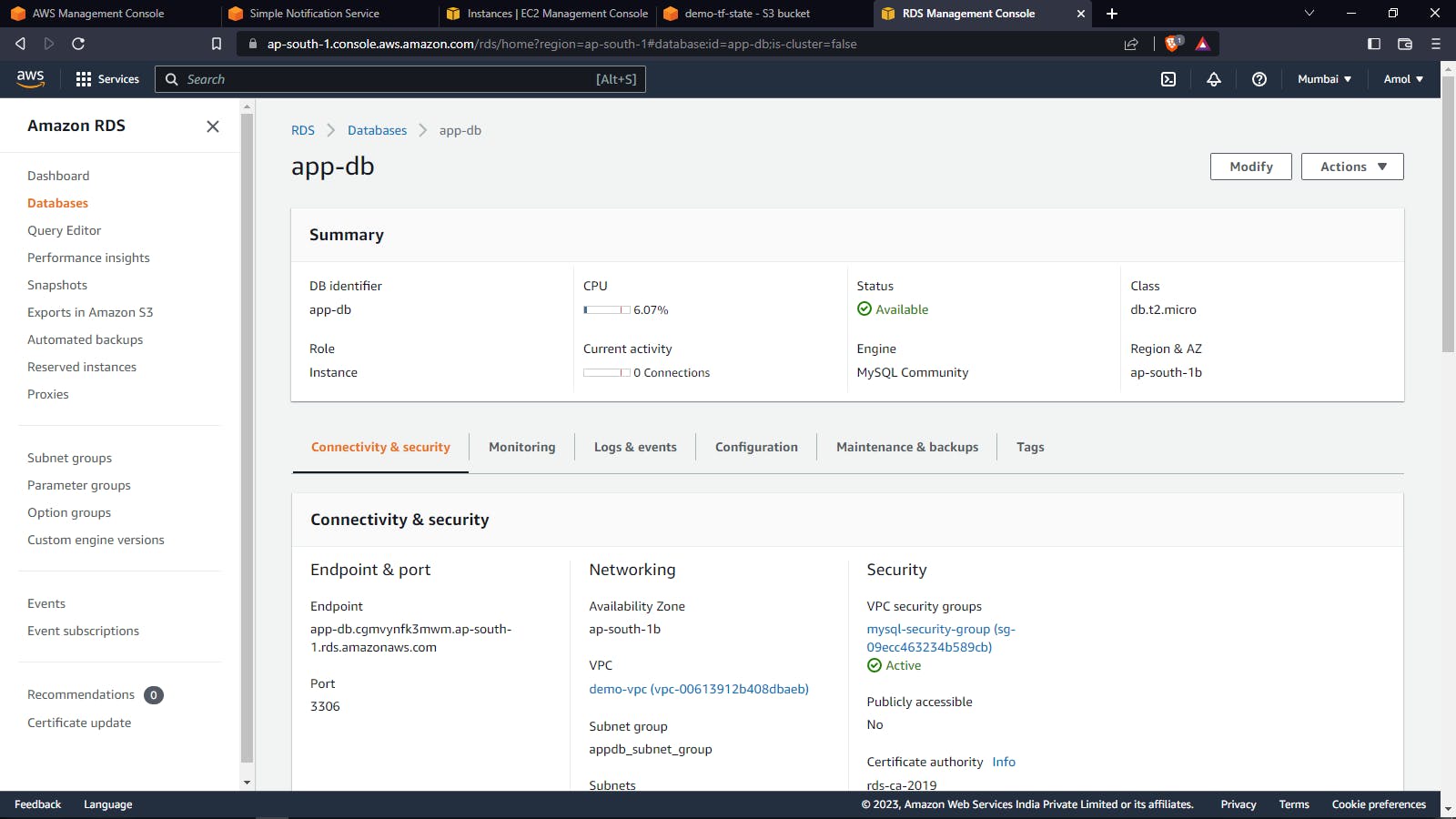
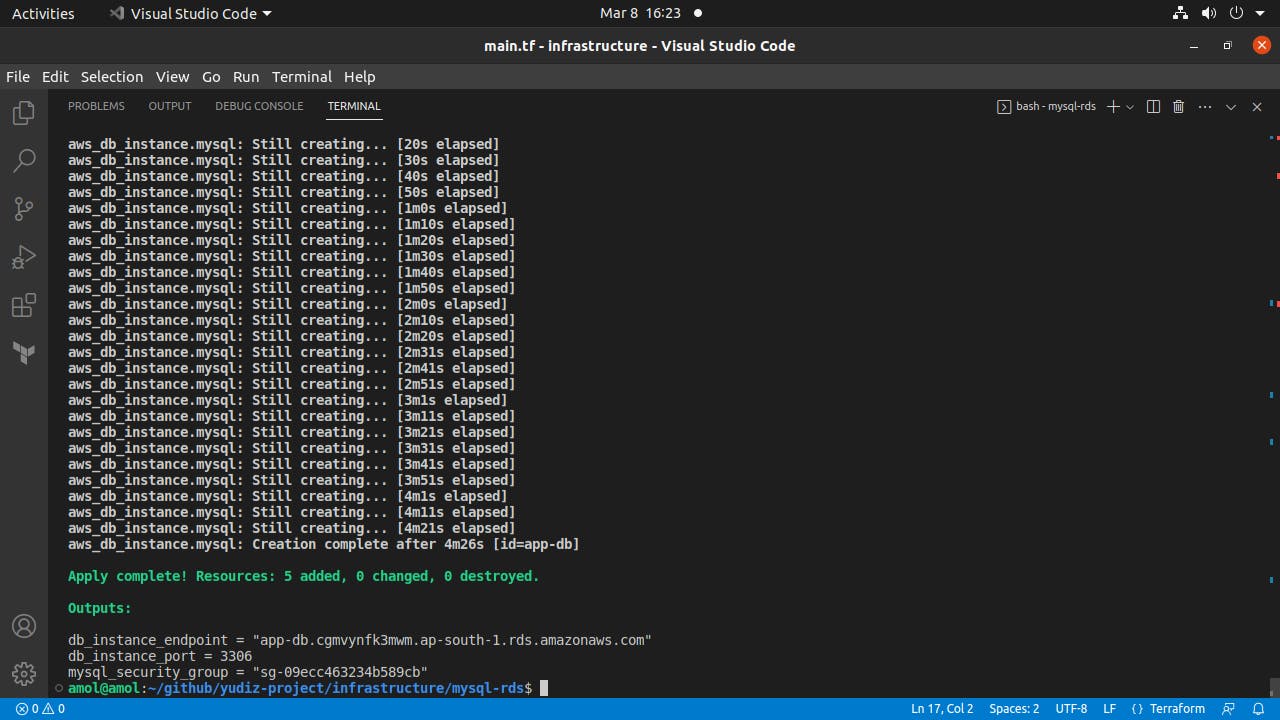
RDS MySQL: Amazon Relational Database Service (RDS) is a fully-managed database service provided by Amazon Web Services (AWS) that makes it easy to set up, operate, and scale a relational database in the cloud. When we use RDS with MySQL, we can easily deploy, configure, and manage a MySQL database instance in the cloud. RDS automates time-consuming tasks such as hardware provisioning, database setup, backups, software patching, and replication.
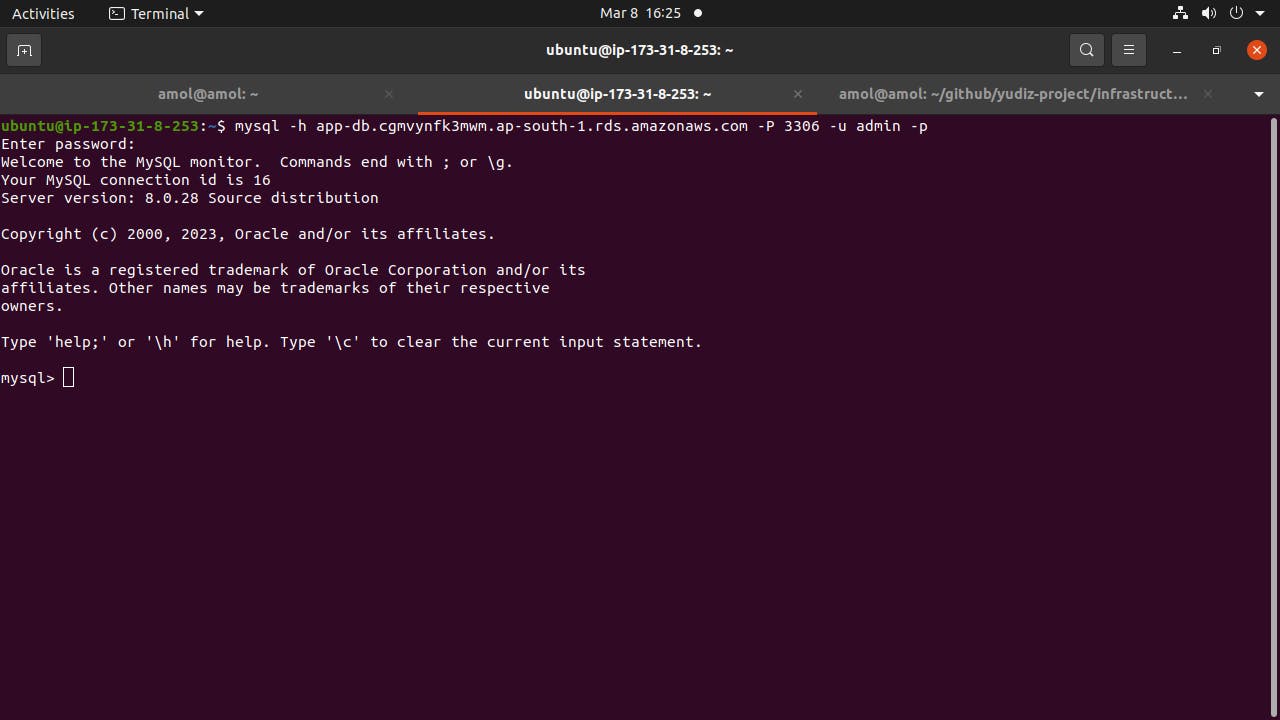
Validating RDS MySQL Connection:
Deploying Spring Boot Application on demo environment created with the help of Ansible:
What is Ansible?
Ansible is an open-source automation tool that enables automate the deployment, configuration, and management of infrastructure, applications, and services. With Ansible, we can write simple, human-readable YAML-based playbooks to describe the tasks and steps needed to automate your environment.
Ansible works by connecting to remote hosts via SSH or other remote APIs and running tasks in a sequential manner, allowing for easy automation of complex tasks across multiple hosts. It uses a push-based model, which means that the Ansible control node pushes the configuration and changes to the remote hosts.
For our project, we did the following things:
Created Ansible Role.
Created Ansible Dynamic Inventory.
Custom Ansible configuration.
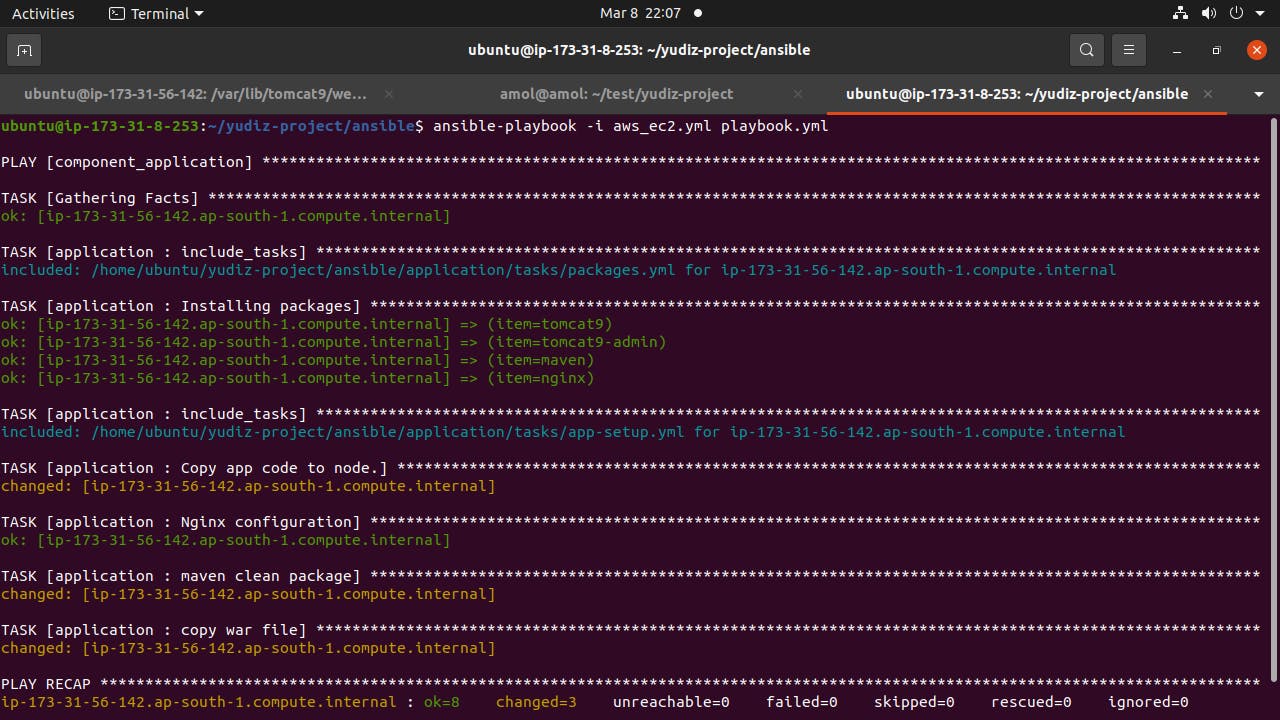
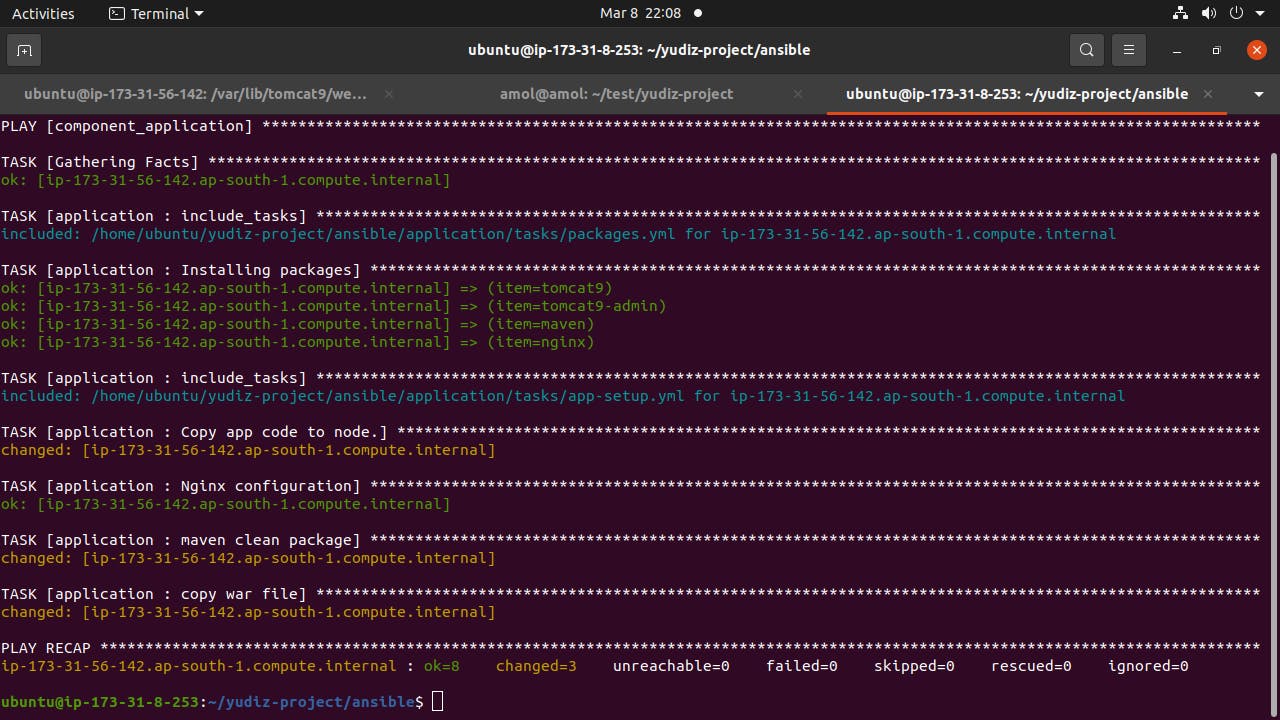
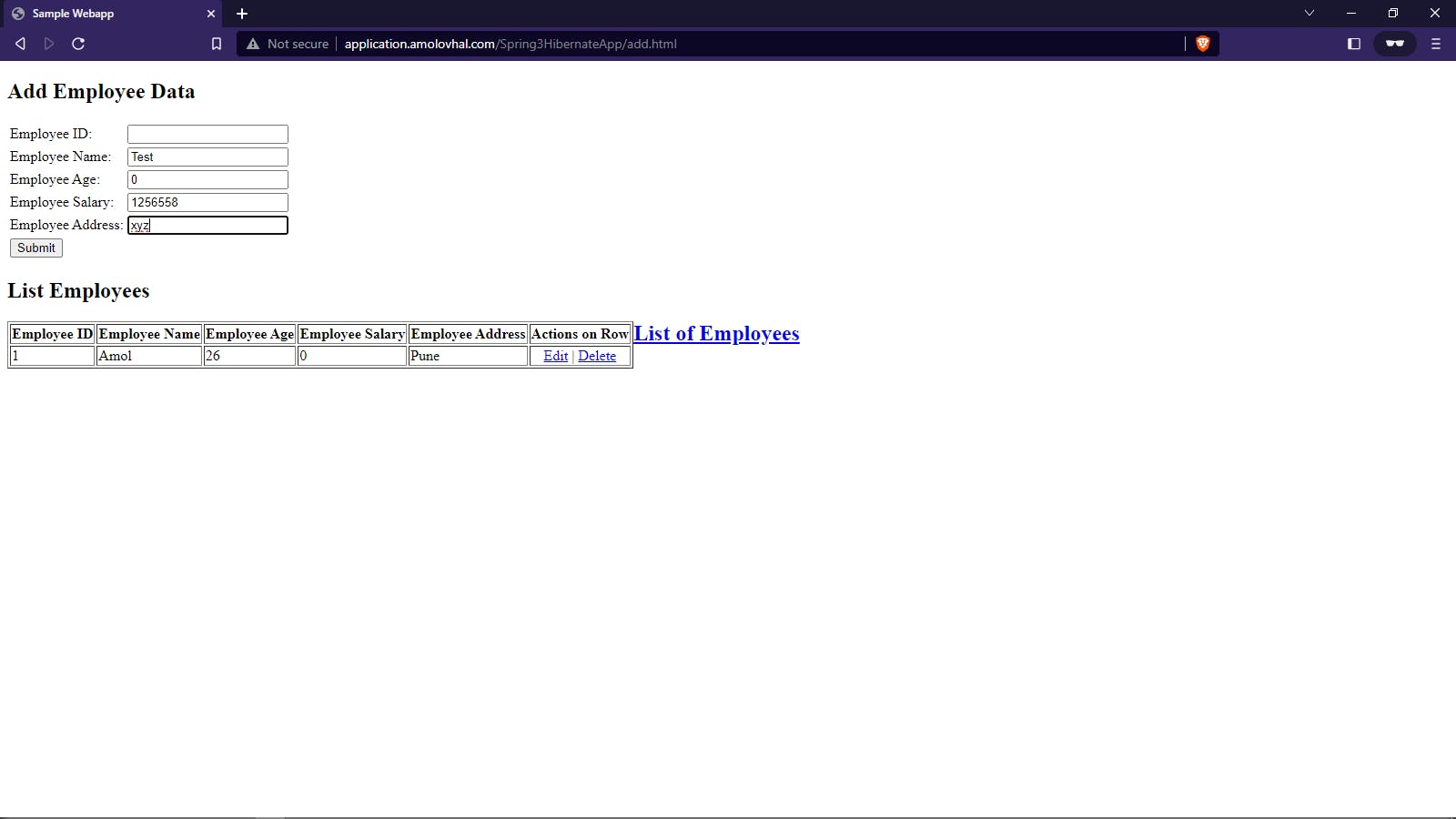
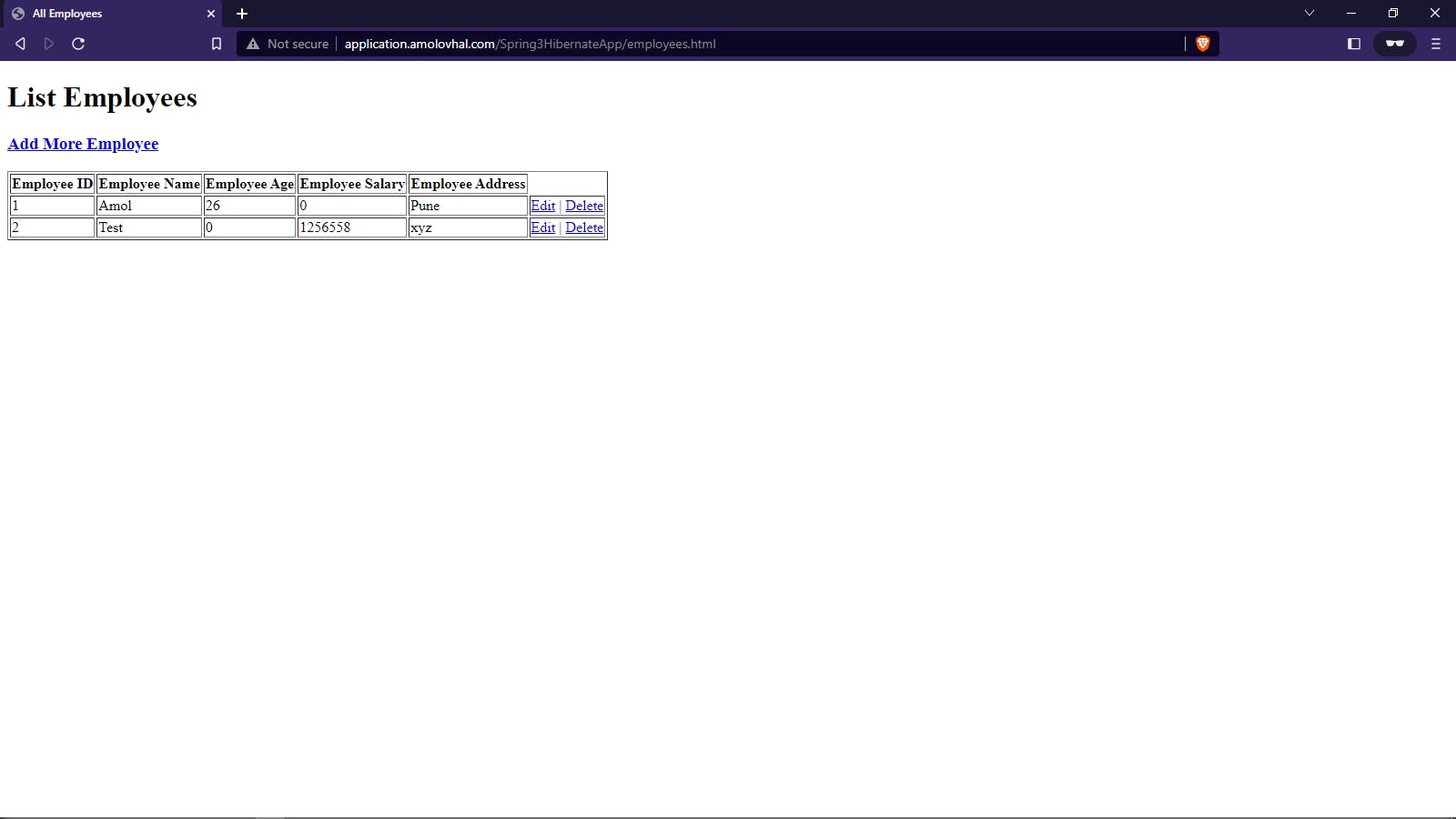
Validating Spring Boot Application:
Application Deployed on URL: http://application.amolovhal.com/Spring3HibernateApp/
The application is validated and the CRUD application is performed.